Instead of having the WriteLog Control Site connect directly to your remote site IP address, you can use a cloud node and a port tunnel. This technique, however, limits the WriteLog audio remoting to TCP only (because UDP packets are not easily routed using SSH tunnels.)
Summary
This page describes a technique requiring an alternative setup at the remote site. putty is the key component of this alternative. Port forwarding is not used at the remote. The control sites see only one difference: the IP address you type in at the control site is the ip address of the SSH server node, not the IP address of the remote.
Use dynamic DNS
This technique uses an SSH server on a third node on the network. That is, its not the remote site, nor the control site. The other two must have a way to connect to the SSH server, and dynamic DNS is a possibility. The most direct network connection from the control site to the remote site is for the remote site to publish its location on the internet to a DNS server. For most of us that would be a dynamic DNS like offered by http://noip.com, but a static IP assignment works as well. WriteLog listens for TCP connections on its three ports. By default, the numbers are 6555 for WriteLog rigs, 6556 for audio and 6557 for RTTY. Typically there is a router at the remote site with a firewall that has to be configured to pass three ports through to the PC running WriteLog.
Tunnel to a rendezvous node
But it might be technically difficult or impossible to arrange for your remote site to be reached that way. Here is an alternative. First you need a site on the internet where you can run an SSH server. For example, http://aws.amazon.com will let you run a limited capacity node for free for a time. I use a paid EC2 instance on the amazon cloud (paid because I am running more than port forwarding.) I run Ubuntu linux on it which comes with http://www.openssh.com. The only difficult part was discovering that, as the putty documentation notes on this page, the openssh server that Ubuntu comes with is openssl. And openssl, by default, does not honor the “Remote ports accept connections from other hosts” option for SSH. You have to login as root on your cloud node and edit the openssl configuration file, /etc/ssh/sshd_config, as documented here. The entry to change is
GatewayPorts yes
On your remote site, you run the free SSH client for Windows, putty, which can set up port forwarding tunnels. You do not need to run a dynamic DNS on your remote site, nor do you need to setup router port forwarding in this configuration. (You likely still need remote desktop access—somebody has to start putty—and some of those products might need a DNS address, but others use a server on the internet like I am describing here for WriteLog.)
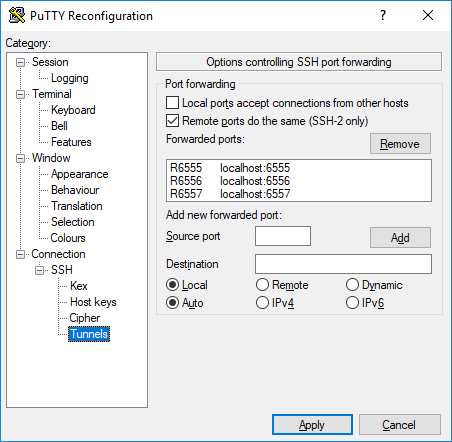
You start remote control by runing PUTTY at the remote site and keep it running as long as you want to remote control WriteLog. With PUTTY you login to your SSH machine on the cloud. PUTTY leaves a command window on your remote PC, but you don’t use the command window while controlling WriteLog. You can’t close its command window (it refuses to close as long as a tunnel is active) but may be minimized to an icon. Your cloud server does need to run dynamic DNS so that both PUTTY at the remote site, and WriteLog at the control site, can rendezvous there. The screen shot shows PUTTY set up to forward the three WriteLog ports, 6555, 6556 and 6557. Step by step its not obvious how to add the port to PUTTY, so here are the steps.
- Bring up PUTTY and, having selected Session in the tree on the left, type into the “Host Name” the IP address of your cloud node. (Presumeably you’re running a dynamic DNS server so use that IP name.) The “Host Name” is also what you type into the WriteLog Control Site “IP Address”
- Don’t click OPEN yet. Instead, use the left tree view to open Connection and then SSH and then Tunnels. That gets you to the screen above.
- From the top: click “Remote ports to the same,” which enables your cloud SSH server to accept connections from the WriteLog Control Site.
- In “Source port” type in
6555 - In “Destination” type in
localhost:6555 - Click the Remote button ON
- Click the ADD button. now you get a new line the box above
- repeat for 6556 and 6557.
As I mentioned above, setting up PUTTY this way was not quite enough. The cloud server I chose by default disables PUTTY’s “Remote ports do the same” option and I had to do the admin task on the clould server to add GatewayPorts yes.
And, to repeat the statement in the opening paragraph, this technique limits WriteLog’s remote audio to the TCP connection option. UDP packets are not routed through the tunnel.
