Here is a step-by-step tutorial to install gpg4win and use it to verify the gpg digital signature on a WriteLog download. These software tools change over time, and they behave differently on different versions of Windows. Therefore, you mileage may vary. This was constructed with Windows 10 in October, 2016.
The first few steps are one time only; in order to get gpg4win installed. At that point your Windows login is a participant in the gpg open source digital signing infrastructure. If you download and install software from the internet—then you really want to know how to use these tools to protect yourself from hackers. If you go through this entire page, you’ll not only have the tools to verify WriteLog downloads, but you’ll also have the tools to verify other digitally signed internet downloads. And you’ll have the tools to encrypt and decrypt emails with others that also participate in this public key infrastructure.
A note about this distributed, freeware infrastructure versus the ones big corporations use. Everything outlined on this page is free for end users. But there are no authorities behind them that you can trust. The only thing you are trusting is the certificates you choose to trust, and in the open source community that creates and maintains the code implementing the encryption algorithms.
There are alternative public key infrastructures and, in order to get started, this tutorial depends on the centralized infrastructure used by Microsoft. The main difference is that (a) developers have to pay to play and (b) there is a “chain” of certificates that are digitally traceable to those taking the money that certify that, to their satisfaction, your certificate is good. Somebody had to pay to get the gpg4win download certificate. The benefit is that the checking of the certificate is built into Windows, which auto-magically tells you who they think wrote the code you are installing—nothing more, nothing less.
That last statement I emphasize again. This whole digital signature song and dance tells you who created the kit you are installing. In particular it does not tell you whether it is safe.
Download and install gpg4win
Go to the gpg4win site and click that download button.
Now we immediately have a security problem. We just downloaded something off the internet. How do we decide whether to trust it? Here is one way, and not the only way, by any means, but it is a way to start if you don’t know how or why you are doing this.
Browse to the downloaded file in Windows Explorer
Now Right mouse click on that file and choose Properties.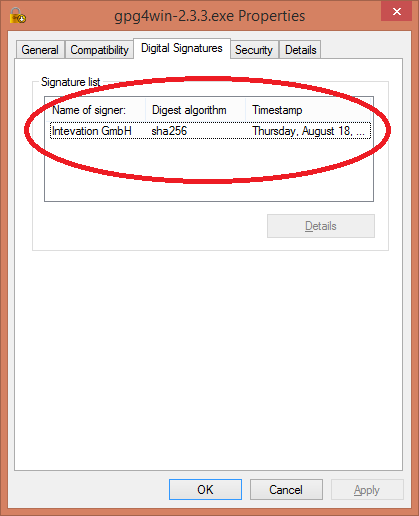 The gpg4win team has complied with the Microsoft security infrastructure and has a Code Signing Certificate, which is displayed as above. For the purpose of this tutorial, we’ll go ahead based on seeing that. You have to make your own security decisions.
The gpg4win team has complied with the Microsoft security infrastructure and has a Code Signing Certificate, which is displayed as above. For the purpose of this tutorial, we’ll go ahead based on seeing that. You have to make your own security decisions.
After a double-click on the installer, we get to this. You had to supply admin credentials to get to that splash screen. At this point, you have not only run downloaded code as your own Windows login, but now you have run it with full admin privileges. Good luck with that.
You had to supply admin credentials to get to that splash screen. At this point, you have not only run downloaded code as your own Windows login, but now you have run it with full admin privileges. Good luck with that.
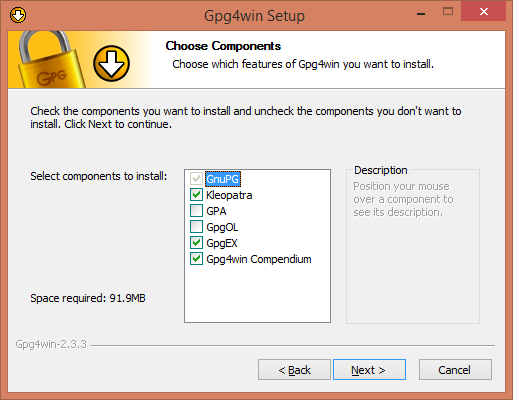 The options I show above must be checked in order to run the rest of this tutorial. You may click additional ones. Browse them to see if there is a feature you want. I skip a few screen shots here—go ahead and finish the install. Then find the Program Group gpg4win and start Kleoptra. That tool is how you manage keys and certificates. It looks like this for a new user.
The options I show above must be checked in order to run the rest of this tutorial. You may click additional ones. Browse them to see if there is a feature you want. I skip a few screen shots here—go ahead and finish the install. Then find the Program Group gpg4win and start Kleoptra. That tool is how you manage keys and certificates. It looks like this for a new user.
Find WriteLog public key
The WriteLog team uses a certain public key to sign all its installable downloads. Your task is to find and trust one. In the pgp infrastructure there is no centrally trusted authority. You have to instead look around and figure out what you trust. Multiple copies of our key are published. All should be identical.
Bought a WriteLog CDROM?
If you purchased WriteLog on a CD that was shipped to you as a physical object, you have a copy of the WriteLogPurchases.asc public key that came to you by mail on a sort-of non-writable medium. We use CDR technolog. Mail can be intercepted and files on CDRs can be replaced. Is that more or less likely than a hacker getting control of writelog.com? You decide.
Note that purchasing and downloading our ISO file to make your own CD does not have the same security implications as using a physical CD we shipped you in the mail.
If you have a CD and choose to trust it, skip the following section and continue at Kleopatra import…
Get the WriteLog public key. Twice
We’ll download the WriteLog public key from WriteLog.com.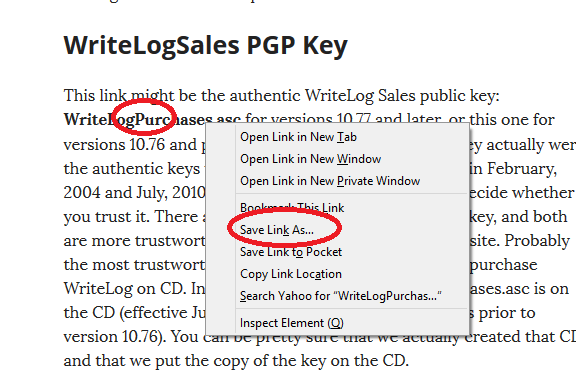
It depends on what browser you are running. In Firefox, right click the link and you get a menu like the above. Choose Save-Link-As.
Kleopatra Import WriteLog public key
Now switch to Kleopatra and use its Import Certificates button, browse to the downloaded ASC file (or the one on your WriteLog CD) and you should get to this screen.
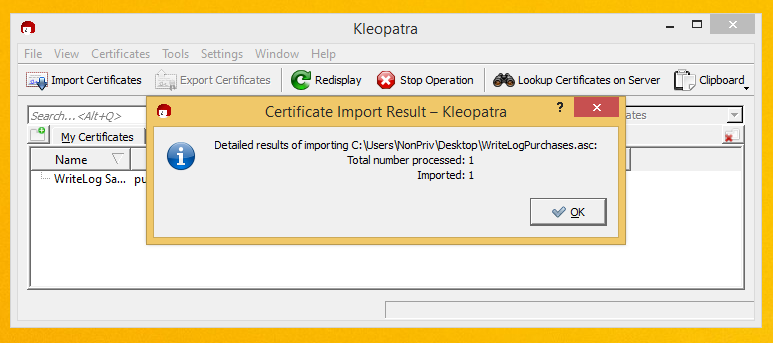
We’re going to get a second copy of the WriteLog Purchases certificate in this tutorial. One good certificate is enough, but how do you know the one you got off writelog.com is not pirated? You don’t. So we’ll get one from somewhere else, too. The pirates would have to compromise two different sites for them to both be bad. Here is how to get the second one. Click on Lookup Certificates on Server.
Oops, Kleopatra won’t let us go there yet:
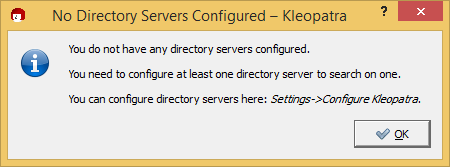
Do what it said to do and you get here: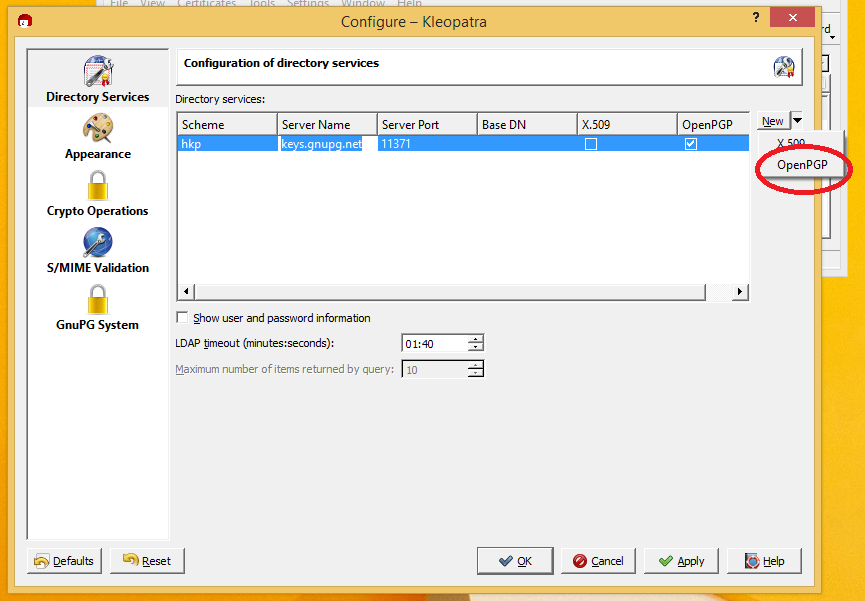 Click on that New button in the upper right and it should fill in the dialog as shown for keys.gnupg.net.
Click on that New button in the upper right and it should fill in the dialog as shown for keys.gnupg.net.
Try a second copy of the WriteLog public key
Now go back to the main Kleopatra screen and click Lookup on Servers again. Type in “writelog” and click Search: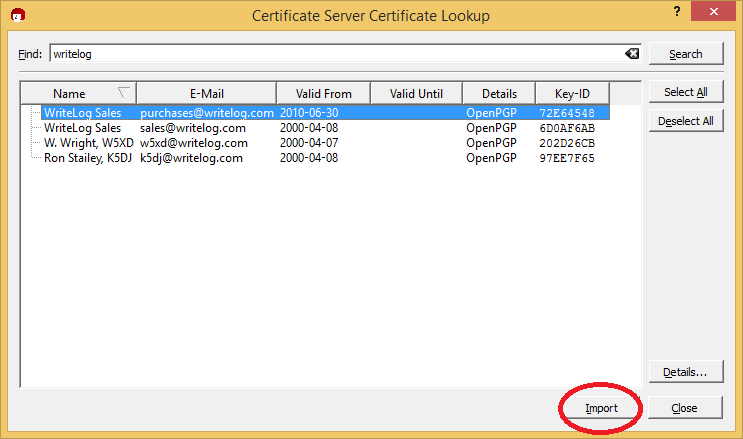 The WriteLog team has published a number of keys. You can safely import any or all of them, but we are interested for now in the one that is used to sign WriteLog downloads. Its the one highlighted in the screen shot above. Import it. (The one for sales@writelog.com has not been used for a long time. You only need it if you’re going to verify very old WriteLog downloads.)
The WriteLog team has published a number of keys. You can safely import any or all of them, but we are interested for now in the one that is used to sign WriteLog downloads. Its the one highlighted in the screen shot above. Import it. (The one for sales@writelog.com has not been used for a long time. You only need it if you’re going to verify very old WriteLog downloads.)
This picture is more important than it looks:
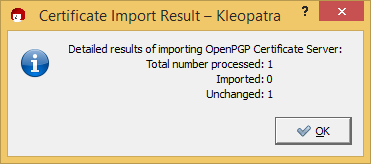
If you get the picture I did, then you see Kleopatra telling you that you just imported a key identical to one you already had. We now have downloaded the WriteLog signing key from two sources and they match. Good for us. Lets tell Kleopatra we trust the certificate.
Right click the newly downloaded certificate.
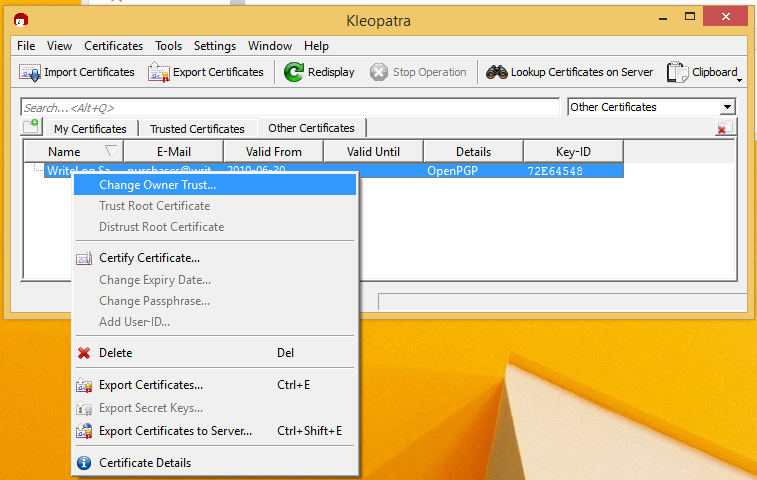
And tell gpg that you trust it.
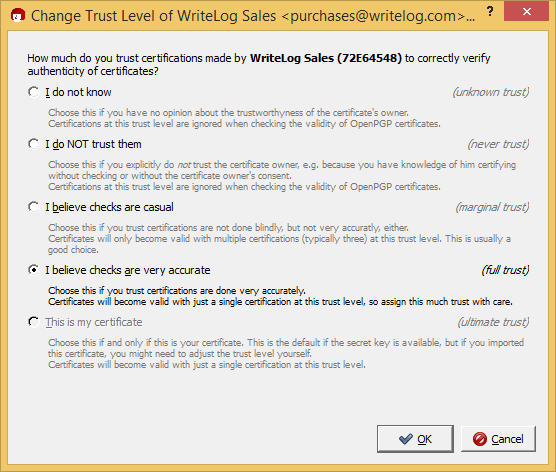
Your mileage may vary. I chose “very accurate” based on having downloaded twice and gotten a match. Make your own choice.
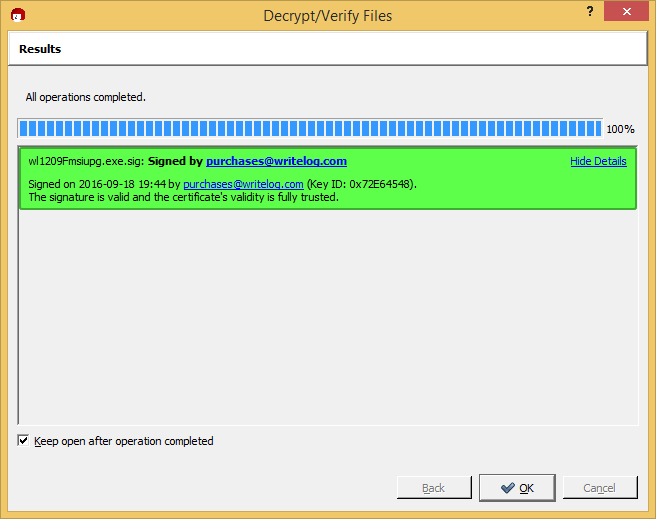
For every download
The WriteLog team publishes a .sig file corresponding to each installable download we publish. Let’s try the one for WriteLog version 12.09F, which happens to be current as I create this tutorial. The keys are published on our archives page.
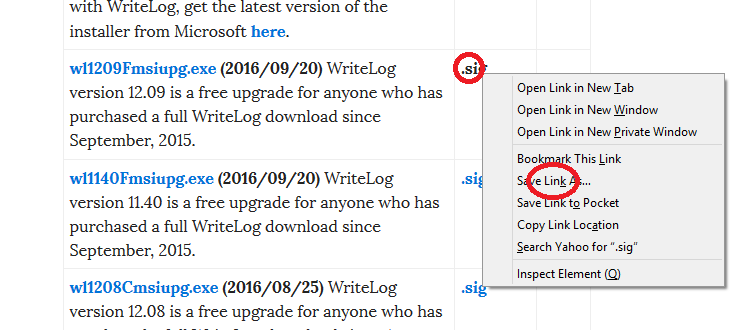
Save that .sig file in the same directory as your WriteLog installer. In my case, the two file names are:
- wl1209Fmsiupg.exe.sig
- wl1209Fmsiupg.exe
The fact that the file names match is important. When, in Windows Explorer, you right mouse click on the .sig file, gpg4win has put new entries, as shown here, in the menus.
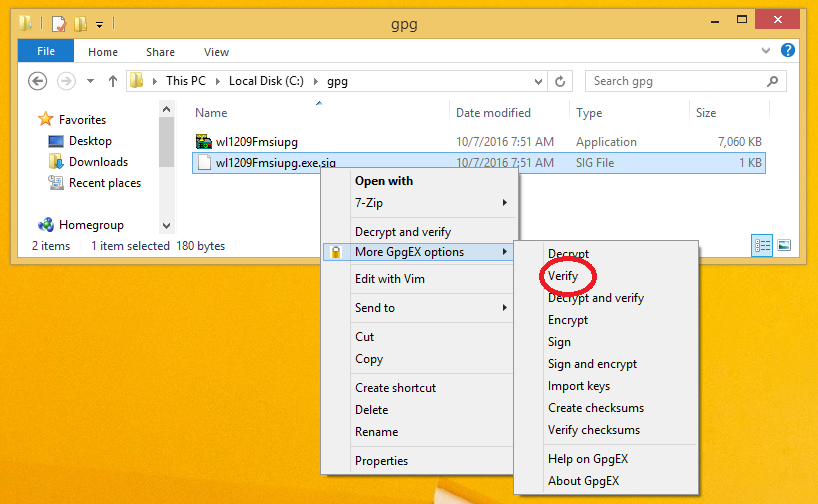
Use the Verify menu entry to get here:
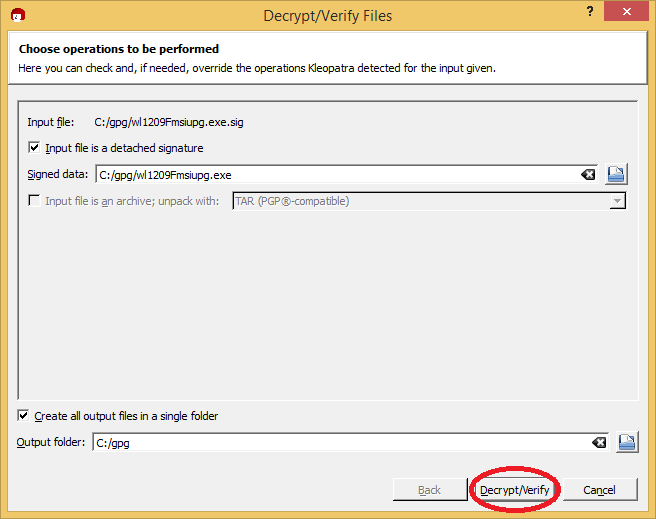
And, unless you have found a hacked download, you’ll get to this screen:
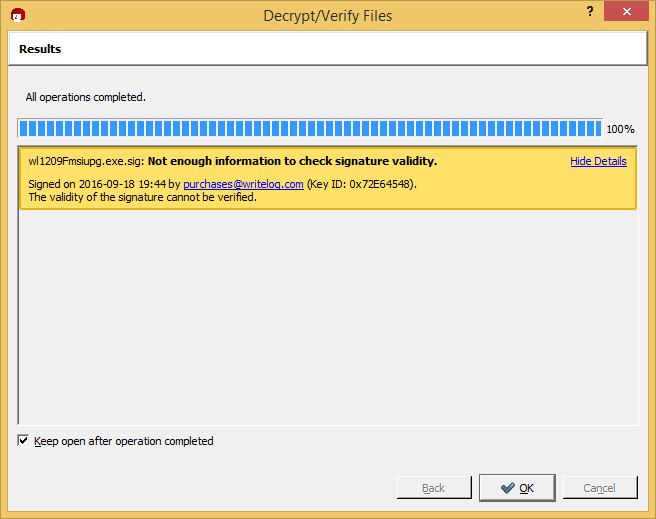
All this work and it still doesn’t tell me the download is OK! Not enough information? Huh?
What is going on?
Establish a GPG identity
This section need only be done once.
The issue with the Not Enough Information is that gpg has verified that the .sig file and the .exe file are indeed a match with respect to the WriteLog Purchases public key. But, before it will be happy (make its screen colored green) it has to believe it knows who “you” are, and that “you” trust that WriteLog public key. Here is how to do that.
Go back to Kleopatra. Click the File/New-Certificate menu.
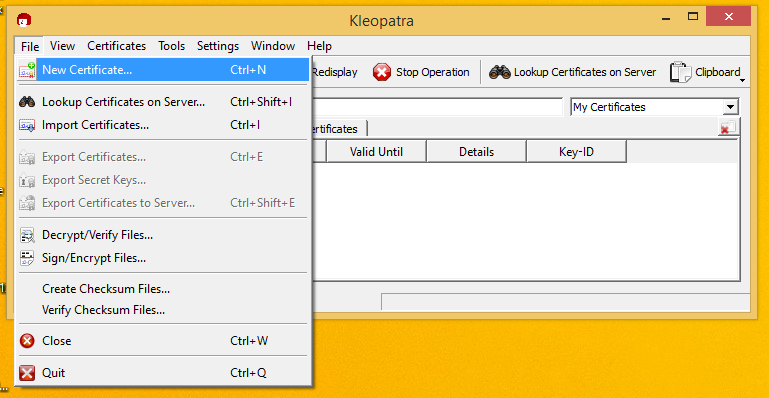
Create a Personal certificate.
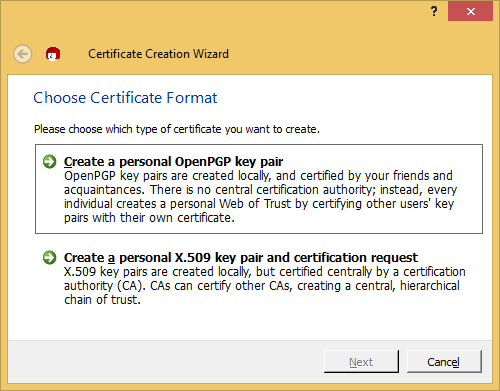
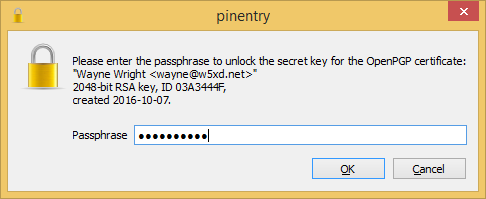
Give it the information it asks for (I skip a screen dump or two.) It will ask you to create a pass phrase for you key. Your pass phrase is a VERY IMPORTANT SECRET. Its secrecy makes it possible for you to be uniquely you in the digital world. Nobody can impersonate you without it. And nobody can recover it for you if you lose it. You have been warned.
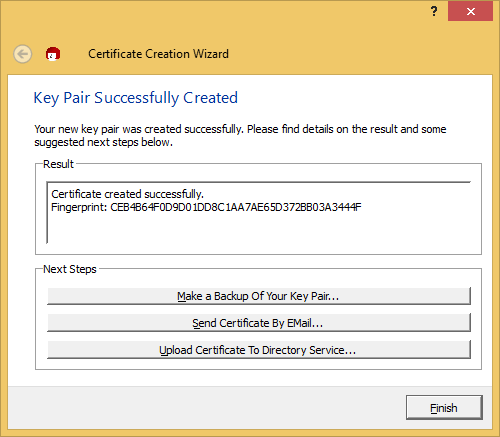
Those optional steps displayed above can be done later. For the purpose of this tutorial, we just Finish.
Then, in the main Kleopatra screen, find the purchases@writelog.com certificate (move to Other Certificates, if necessary) and double click it.
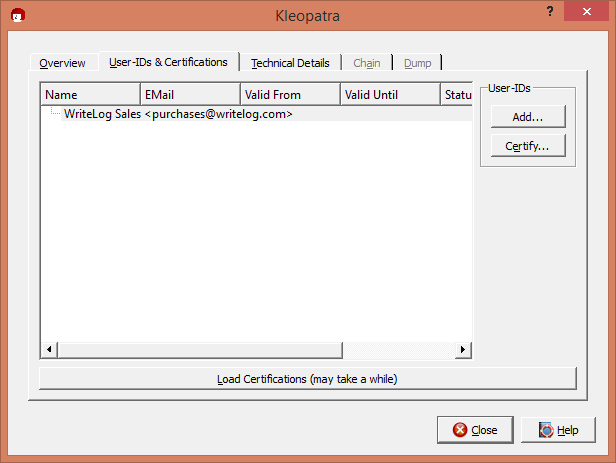
Click Certify.
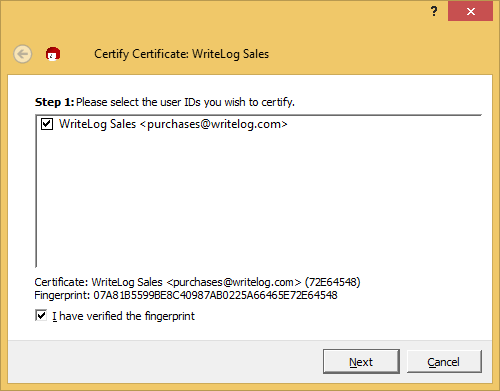
Next.
Then, click Only Me:
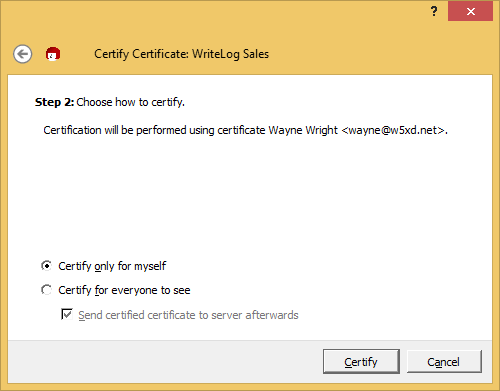
You now have prove to gpg that you are who you say you are.
From now on, when you verify a WriteLog purchases signature, you should get a green indicator like this: